在kubernetes中部署企业级ELK并使用其APM
一、架构为了增加es的扩展性 , 按角色功能分为master节点、data数据节点、client客户端节点 。 其整体架构如下: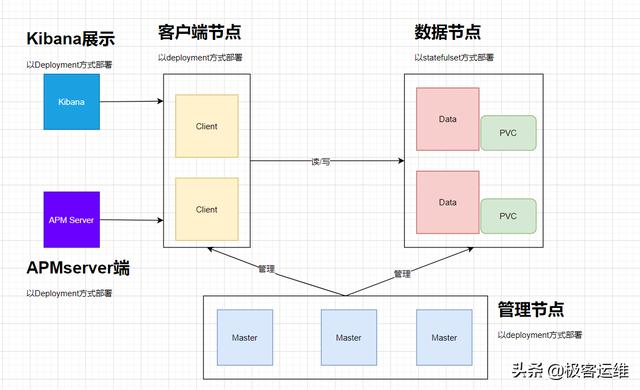 文章插图
文章插图
其中:
- Elasticsearch数据节点Pods被部署为一个有状态集(StatefulSet)
- Elasticsearch master节点Pods被部署为一个Deployment
- Elasticsearch客户端节点Pods是以Deployment的形式部署的 , 其内部服务将允许访问R/W请求的数据节点
- Kibana和APMServer部署为Deployment , 其服务可在Kubernetes集群外部访问
二、部署ES先创建estatic的命名空间(es-ns.yaml):
apiVersion: v1kind: Namespacemetadata:name: elastic执行kubectl apply -f es-ns.yaml2.1、生成证书启动es的xpack功能 , 传输需要加密传输 。 脚本如下(es-create-ca.sh):
#!/bin/bash# 指定 elasticsearch 版本RELEASE=7.8.0# 运行容器生成证书docker run --name elastic-charts-certs -i -w /app \elasticsearch:${RELEASE} \/bin/sh -c " \elasticsearch-certutil ca --out /app/elastic-stack-ca.p12 --pass ''--tt-darkmode-color: #35B378;">2.1、部署es master节点配置清单如下(es-master.yaml):
---apiVersion: v1kind: ConfigMapmetadata:namespace: elasticname: elasticsearch-master-configlabels:app: elasticsearchrole: masterdata:elasticsearch.yml: |-cluster.name: ${CLUSTER_NAME}node.name: ${NODE_NAME}discovery.seed_hosts: ${NODE_LIST}cluster.initial_master_nodes: ${MASTER_NODES}network.host: 0.0.0.0node:master: truedata: falseingest: falsexpack.security.enabled: truexpack.monitoring.collection.enabled: truexpack.security.transport.ssl.enabled: truexpack.security.transport.ssl.verification_mode: certificatexpack.security.transport.ssl.keystore.path: /usr/share/elasticsearch/config/certs/elastic-certificates.p12xpack.security.transport.ssl.truststore.path: /usr/share/elasticsearch/config/certs/elastic-certificates.p12xpack.ml.enabled: truexpack.license.self_generated.type: basicxpack.monitoring.exporters.my_local:type: localuse_ingest: false---apiVersion: v1kind: Servicemetadata:namespace: elasticname: elasticsearch-masterlabels:app: elasticsearchrole: masterspec:ports:- port: 9300name: transportselector:app: elasticsearchrole: master---apiVersion: apps/v1kind: Deploymentmetadata:namespace: elasticname: elasticsearch-masterlabels:app: elasticsearchrole: masterspec:replicas: 1selector:matchLabels:app: elasticsearchrole: mastertemplate:metadata:labels:app: elasticsearchrole: masterspec:initContainers:- name: init-sysctlimage: busybox:1.27.2command:- sysctl- -w- vm.max_map_count=262144securityContext:privileged: truecontainers:- name: elasticsearch-masterimage: docker.elastic.co/elasticsearch/elasticsearch:7.8.0env:- name: CLUSTER_NAMEvalue: elasticsearch- name: NODE_NAMEvalue: elasticsearch-master- name: NODE_LISTvalue: elasticsearch-master,elasticsearch-data,elasticsearch-client- name: MASTER_NODESvalue: elasticsearch-master- name: "ES_JAVA_OPTS"value: "-Xms512m -Xmx512m"ports:- containerPort: 9300name: transportvolumeMounts:- name: configmountPath: /usr/share/elasticsearch/config/elasticsearch.ymlreadOnly: truesubPath: elasticsearch.yml- name: storagemountPath: /data- name: localtimemountPath: /etc/localtime- name: keystoremountPath: /usr/share/elasticsearch/config/certs/elastic-certificates.p12readOnly: truesubPath: elastic-certificates.p12volumes:- name: configconfigMap:name: elasticsearch-master-config- name: "storage"emptyDir:medium: ""- name: localtimehostPath:path: /etc/localtime- name: keystoresecret:secretName: elastic-certificatesdefaultMode: 044然后执行kubectl apply -f ``es-master.yaml创建配置清单 , 然后pod变为running状态即为部署成功 。
# kubectl get pod -n elasticNAMEREADYSTATUSRESTARTSAGEelasticsearch-master-77d5d6c9db-xt5kq1/1Running067s2.2、部署es data节点配置清单如下(es-data.yaml):
---apiVersion: v1kind: ConfigMapmetadata:namespace: elasticname: elasticsearch-data-configlabels:app: elasticsearchrole: datadata:elasticsearch.yml: |-cluster.name: ${CLUSTER_NAME}node.name: ${NODE_NAME}discovery.seed_hosts: ${NODE_LIST}cluster.initial_master_nodes: ${MASTER_NODES}network.host: 0.0.0.0node:master: falsedata: trueingest: falsexpack.security.enabled: truexpack.monitoring.collection.enabled: truexpack.security.transport.ssl.enabled: truexpack.security.transport.ssl.verification_mode: certificatexpack.security.transport.ssl.keystore.path: /usr/share/elasticsearch/config/certs/elastic-certificates.p12xpack.security.transport.ssl.truststore.path: /usr/share/elasticsearch/config/certs/elastic-certificates.p12xpack.ml.enabled: truexpack.license.self_generated.type: basicxpack.monitoring.exporters.my_local:type: localuse_ingest: false---apiVersion: v1kind: Servicemetadata:namespace: elasticname: elasticsearch-datalabels:app: elasticsearchrole: dataspec:ports:- port: 9300name: transportselector:app: elasticsearchrole: data---apiVersion: apps/v1kind: StatefulSetmetadata:namespace: elasticname: elasticsearch-datalabels:app: elasticsearchrole: dataspec:serviceName: "elasticsearch-data"selector:matchLabels:app: elasticsearchrole: datatemplate:metadata:labels:app: elasticsearchrole: dataspec:initContainers:- name: init-sysctlimage: busybox:1.27.2command:- sysctl- -w- vm.max_map_count=262144securityContext:privileged: truecontainers:- name: elasticsearch-dataimage: docker.elastic.co/elasticsearch/elasticsearch:7.8.0env:- name: CLUSTER_NAMEvalue: elasticsearch- name: NODE_NAMEvalue: elasticsearch-data- name: NODE_LISTvalue: elasticsearch-master,elasticsearch-data,elasticsearch-client- name: MASTER_NODESvalue: elasticsearch-master- name: "ES_JAVA_OPTS"value: "-Xms1024m -Xmx1024m"ports:- containerPort: 9300name: transportvolumeMounts:- name: configmountPath: /usr/share/elasticsearch/config/elasticsearch.ymlreadOnly: truesubPath: elasticsearch.yml- name: elasticsearch-data-persistent-storagemountPath: /data/db- name: keystoremountPath: /usr/share/elasticsearch/config/certs/elastic-certificates.p12readOnly: truesubPath: elastic-certificates.p12volumes:- name: configconfigMap:name: elasticsearch-data-config- name: keystoresecret:secretName: elastic-certificatesdefaultMode: 044volumeClaimTemplates:- metadata:name: elasticsearch-data-persistent-storagespec:accessModes: [ "ReadWriteOnce" ]storageClassName: managed-nfs-storageresources:requests:storage: 20Gi---
- 麒麟|荣耀新款,麒麟810+4800万超清像素,你还在犹豫什么呢?
- 智能手机市场|华为再拿第一!27%的份额领跑全行业,苹果8%排在第四名!
- 空调|让格力、海尔都担忧,中国取暖“新潮物”强势来袭,空调将成闲置品?
- 行业|现在行业内客服托管费用是怎么算的
- 国外|坐拥77件专利,打破国外的垄断,造出中国最先进的家电芯片
- 零部件|马瑞利发力电动产品,全球第七大零部件供应商在转型
- 手机基带|为了5G降低4G网速?中国移动回应来了:罪魁祸首不是运营商
- 通气会|12月4~6日,2020中国信息通信大会将在成都举行
- 中国|浅谈5G移动通信技术的前世和今生
- 俄罗斯手机市场|被三星、小米击败,华为手机在俄罗斯排名跌至第三!
